Information security risk management framework
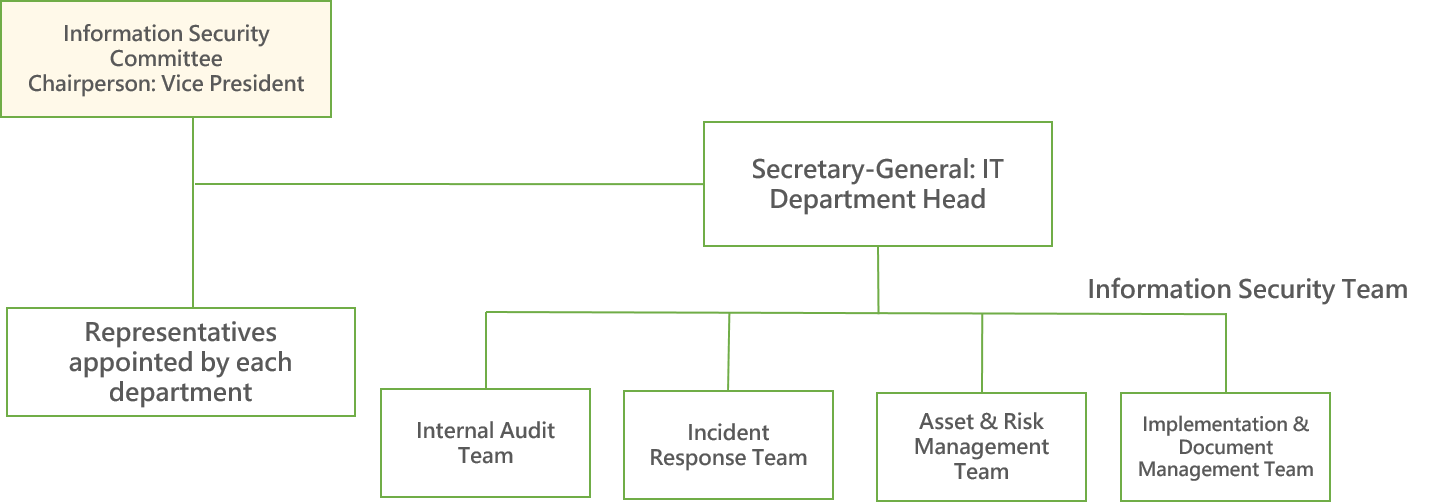
To enhance information security operations and management, the company has established a cross-departmental Information Security Committee. This committee formulates information security management policies, promotes the Information Operations Procedures, coordinates cross-departmental information processing workflows, reviews the company's information security policies and execution outcomes, and regularly reports the company's cybersecurity governance status to the board of directors.
The organizational structure of the Information Security Committee is as follows:
Information Security Policy Objectives
"Implement information security, reduce cybersecurity risks, increase customer trust, and improve operational performance."
To strengthen information security management and ensure the effective operation of management systems, the company is committed to protecting the confidentiality, integrity, and availability of its information assets. A policy framework is specifically established to provide the security management required for the company’s continuous operations, with the goal of sustainable development and compliance with relevant regulations.To strengthen information security management and ensure the effective operation of the management system, the company establishes policies to safeguard the confidentiality, integrity, and availability of its information assets. These policies provide security management to ensure business continuity, achieve sustainable operations, and comply with relevant regulations.
The company is actively implementing and establishing a comprehensive Information Security Management System (ISMS), forming a cross-functional information security organization to ensure business continuity, executing information security risk assessment mechanisms, enhancing information security management effectiveness, and implementing internal information security audits to ensure the effectiveness of security measures. The company supports the continuous development and sustainable operation of the group, ensuring that business activities comply with policies, laws, and regulations. Through a continuous Plan-Do-Check-Act (PDCA) approach, the company ensures the effective operation of the system, maintains proper documentation or system records of activities, and evaluates and verifies any incidents or anomalies in accordance with established procedures.
Information security management measures
| Categories | Description | Related Procedures |
|---|---|---|
|
Authorization Management |
Management of each system account and authorization |
|
|
Accessibility Management |
Access management Access to internal and external data, letter transmission, control through filtering |
|
|
External Prevention |
Network security, anti-virus software, outsourcing and third-party supplier |
|
|
System Repair |
System usage status, handling measures for disconnection |
|
|
Database management |
Database backup |
|
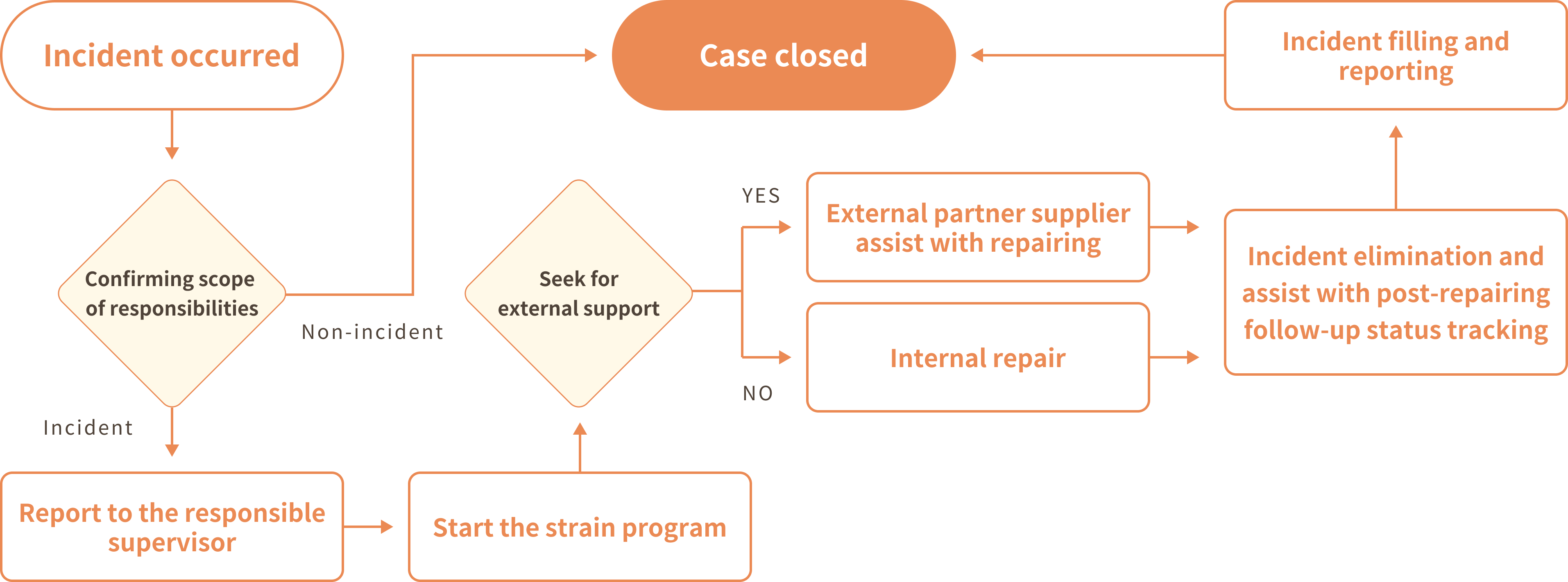
The emergency strain plan of the company's information system is as follows. The reporting and handling of information security incidents should all be performed in compliance with the procedures.
Resources Invested in Information Security Management and Execution Status
1. Since the establishment of the Information Security Committee in September 2019, the company has held regular quarterly meetings.
2. In 2024, the committee held four meetings on March 7, June 6, September 5, and December 12.
3. In 2024, key cybersecurity topics and incidents addressed included equipment failure drills, social engineering drills, cybersecurity training, privilege account audits, unauthorized software checks, and information security risk assessments.
4. In 2023, the Information Security Committee approved the adoption of ISO 27001:2022, which was formally implemented in 2024. An internal audit was completed in October, and a management review meeting was held on November 15.
5. In accordance with Financial Supervisory Commission (FSC) regulations, the company appointed one Chief Information Security Officer (CISO) and one cybersecurity personnel in 2023. In 2024, they obtained certification, meeting regulatory requirements.
6. The implementation status of information security was reported at the 5th meeting of the 8th Board of Directors on December 21, 2024.
Information Security Incident Status
In 2024, no major information security incidents occurred. Additionally, there were no breaches of confidential information affecting customer or employee personal data, nor any incidents leading to penalties.

